IOT-devices are insecure and exist in every modern home:
With the enormous amount of connected small IOT-devices in peoples’ homes, I think it’s becoming more and more important to separate “dumb IOT” devices that are usually not receiving security/firmware updates a moment after they’ve been bought. Examples of such devices can be old phones/tablets, outdated but still used security cameras, temperature sensors, outdated routers, media/gaming devices etc. Many normal people don’t don’t care much about the risks associated with having insecure devices connected to their primary computer network – especially people not in the IT industry… Luckily it’s however pretty standard to have a builtin firewall in consumer routers.
How many years did it take for me to understand why I needed the solution I have today?
My personal journey with firewalls started probably around 10-15 years ago with https://dd-wrt.com/ because at that time I was also interested in OSS (Open Source Software) and DDWRT. So I bought myself a cheap router of this type: https://en.wikipedia.org/wiki/Linksys_WRT54G_series – and it seemed nice (but wasn’t and that took some years to understand). Back in those days we hadn’t all the options we have today, but the combination of installing a custom firmware on my router opened up for learning and doing more advanced networking things than what is typically possible on consumer routers – and what consumers typically do… So that has shaped me and what I know about networking today…
I could now install a lot of simple Linux packages using e.g. https://wiki.dd-wrt.com/wiki/index.php/Ipkg and https://wiki.dd-wrt.com/wiki/index.php/Installing_Entware on my home router – “wow – that was crazy insane”, I thought… I began to learn a lot of new advanced things about routers and networking, by reading in the corresponding forums, asking questions and so on. After some years I upgraded to the following by still basically similar concept as with DDWRT/AsusWRT):
- https://www.tp-link.com/us/support/download/tl-wr1043nd/
- https://www.asus.com/us/networking-iot-servers/wifi-routers/asus-wifi-routers/rtac87u/ (flashed to https://www.asuswrt-merlin.net/)
- https://www.netgear.com/dk/home/wifi/routers/r7000/
IOT-devices have been around for some years and often these devices rarely receive security firmware updates unlike those we receive on our laptops (Windows Update etc). I think for the past 6-7 years, I obtained an understanding I didn’t have earlier of why I needed to use VLANs to segment my network traffic and I’ll try to convey that understanding below:
What is VLAN segmentation?
Most people know that a LAN is what’s typically behind their (often ISP-supplied) router and WAN is what’s on the other side of the router, i.e. the internet. It doesn’t take long before one learns that router firewalls typically prevents internet traffic from the WAN (outside) to directly connect to anything on the LAN (inside). The firewall typically blocks traffic in one direction (WAN->LAN), but allows everything in the other direction (LAN->WAN). This is the basic concept of a firewall…
A VLAN is a virtual LAN – so instead of having a single LAN we have multiple LANs. We then configure the firewall rules such that e.g. one network of connected internet-devices (e.g. IOT-devices) is only allowed to have traffic forwarded to the outside (the WAN/internet) – but not to any other internally connected devices. This provides protection against hackers, security threats and malware risks because as soon as anyone (or anything, i.e. malware-infected IOT-devices) have access to your LAN, that device can be used to circumvent the firewall and gain access to other machines or maybe if it’s infected by malware it’ll try to spread to different machines. Software vulnerabilities are found every day and security patches are made to protect systems from being compromised. That was the short story…
Understanding the mistakes I did and why I wish I understood the solution to my problems earlier…
For many years I used DDWRT and AsusWRT for setting up VLAN segmentation on my routers – most importantly to setup:
- a management VLAN (“only for administration of the router”)
- a VLAN for IOT-devices (=”insecure devices” that never received security updates, e.g. old mobile phones with no software updates, old cameras, internet-connected temperature sensors/heating control, smart-TV etc)
- a VLAN for desktop and laptop PC’s, printer (“trusted devices” – those that receive security patches and updates, i.e. Windows/Linux – newest Android-phone/tablet)
For many years DDWRT had a problem with their GUI in the sense that it couldn’t be used for really setting up and configuring VLANs – it was broken, but partly worked. Command-line configuration and startup scripts was needed. It was the same with AsusWRT. I spend hundreds (if not thousands) of hours reading, experimenting and asking in the forums about which (often hardware)-specific commands were needed for assigning e.g. VLAN xx to physical port yy of the router. And there were many bugs that prevented solutions that worked on one specific router from working on my router – so it was a real pain!
I’m sometimes stubborn when it comes to learning about IT and IT technologies – but this was just stupid and a complete waste of my time: I spend several years fine-tuning my VLAN-setup on these flashed EEPROM custom-firmware routers and once in a while I read about people having a more advanced setup on another hardware-platform than I was used to… Unfortunately it took me too many years to understand that I should’ve taken this path a lot earlier so I highly recommend:
I recommend setting up either a pfSense or OPNsense firewall (optionally virtualized) instead of doing the mistakes I did:
For too many years I ignored people writing in the networking-forums about: “oh, and then I also have a pfSense-box which I’m using for controlling my firewall”. I thought that such a firewall was only for businesses, not really for simple consumers as myself and I also thought my dead-cheap home router was good enough, because I was clever enough to “tame it”. I didn’t until the end, consider the hundreds of thousands of hours I struggled with fine-tuning the setup – and when all the wasted hours are taken into account, it’s much better to buy a low-power computer, install pfSense on it – and use that graphical and super-easy GUI to do everything in a very intuitive way. What I took years to achieve on DDWRT/AsusWRT took 1-2 months to achieve on pfSense – but after 2 months, the pfSense-setup was even more advanced and superior.
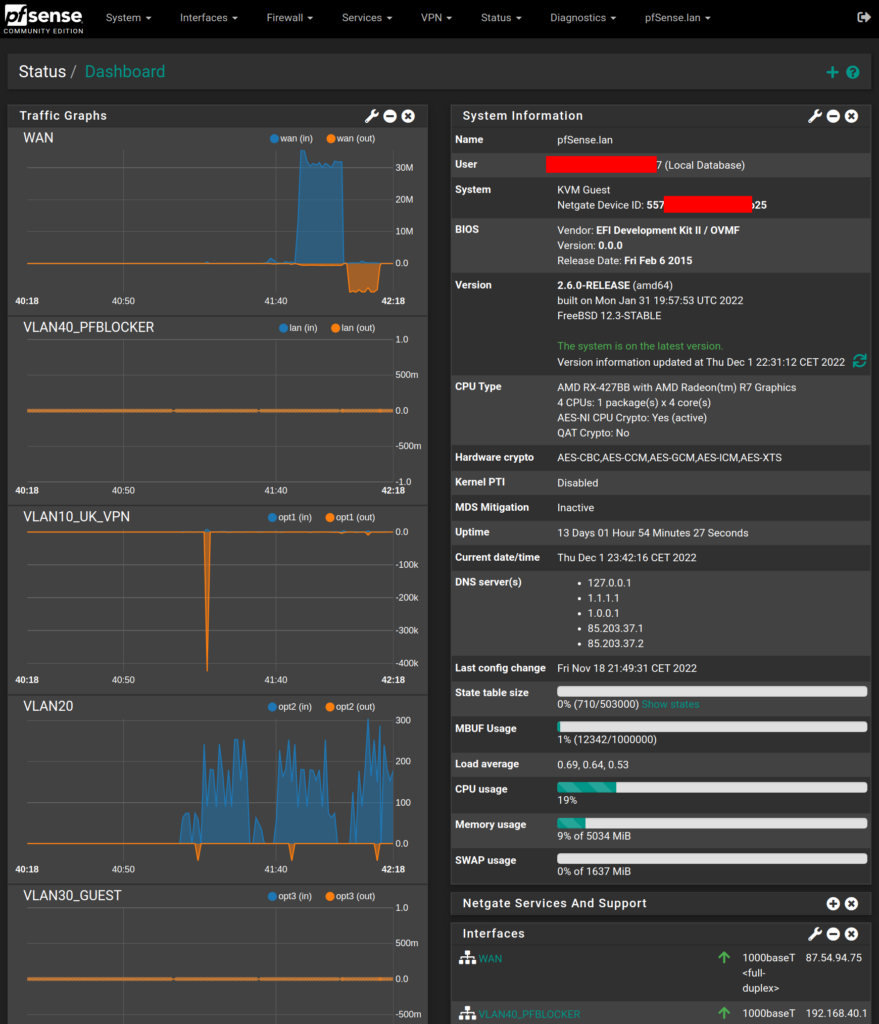
I currently have around 42 internet-connected devices on my network (pfSense -> Status -> DHCP Leases). I’ll explain more about some of the technical details in my next blog post, shortly as this introduction became much longer than I originally anticipated and it’s getting late now.
One reply on “Why I think everyone should do network segmentation (part 1/2)”
Hurray, this is just the right information that I needed. You make me want to learn more! Stop by my page UY4 about Content Writing.